Proxy + LDAP & LDAPS Application Case #
Background #
SphereEx-DBPlusEngine adds support for LDAP login authentication. The following application case shows the use process of LDAP login authentication.
In the process of case display, Wireshark tool is used to capture packets to more vividly show the difference between LDAP and LDAPS protocols.
LDAPS is an LDAP communication mode based on SSL/TLS.
Basic Environment #
| Name | Version |
|---|---|
| MySQL | 5.7 or 8.0 |
| SphereEx DBPlusEngine | 1.0 |
| Wireshark | 3.6 |
| ApacheDS | 2.0.0 |
- config-sharding-databases.yaml
schemaName: sharding_db
dataSources:
ds_0:
url: jdbc:mysql://127.0.0.1:3306/demo_ds_0?serverTimezone=UTC&useSSL=false
username: root
password:
connectionTimeoutMilliseconds: 30000
idleTimeoutMilliseconds: 60000
maxLifetimeMilliseconds: 1800000
maxPoolSize: 10
minPoolSize: 1
ds_1:
url: jdbc:mysql://127.0.0.1:3306/demo_ds_1?serverTimezone=UTC&useSSL=false
username: root
password:
connectionTimeoutMilliseconds: 30000
idleTimeoutMilliseconds: 60000
maxLifetimeMilliseconds: 1800000
maxPoolSize: 10
minPoolSize: 1
rules:
- !SHARDING
tables:
t_order:
actualDataNodes: ds_${0..1}.t_order
keyGenerateStrategy:
column: order_id
keyGeneratorName: snowflake
defaultDatabaseStrategy:
standard:
shardingColumn: user_id
shardingAlgorithmName: database_inline
defaultTableStrategy:
none:
shardingAlgorithms:
database_inline:
type: INLINE
props:
algorithm-expression: ds_${user_id % 2}
keyGenerators:
snowflake:
type: SNOWFLAKE
LDAP Server Configuration #
Adopt Docker image of ApacheDS™: tremolosecurity/apacheds。
a. Pull image.
docker pull tremolosecurity/apacheds:latest
b. Generate SSL certificate.
Description page: https://directory.apache.org/apacheds/basic-ug/3.3-enabling-ssl.html
Use keytool to generate the certificate according to the method in the page.
Take Common name as localhost as an example to generate two files:
.
├── localhost.ks
└── localhost.cer
Because the container used has special requirements for file names, rename localhost.ks as apacheds.jks.
.
├── apacheds.jks
└── localhost.cer
Note: The certificate file can be saved in any path, such as:
- /Users/${yourname}/apacheds/apacheds.jks
- /Users/${yourname}/apacheds/localhost.cer
c. Start container.
docker run --detach --rm --name apacheds \
-p 10389:10389 \
-p 10636:10636 \
-v /Users/${yourname}/apacheds:/etc/apacheds \
-e APACHEDS_ROOT_PASSWORD=secret \
-e APACHEDS_TLS_KS_PWD=secret \
tremolosecurity/apacheds:latest
Notes:
- The container maps two ports, of which 10389 is used as LDAP non encrypted connection and 10636 is used as LDAPS encrypted connection.
- ApacheDS service contains a default user uid=admin, ou=system, which can be accessed through the parameter APACHEDS_ROOT_PASSWORD and its password is secret.
After starting the operation, check whether the log is normal:
docker logs -f apacheds
d. ldapsearch test
The ldapsearch command can easily initiate access to the LDAP service and verify whether the LDAP service is normal:
docker exec -it apacheds ldapsearch -x -H ldap://localhost:10389 -b ou=system -D "uid=admin,ou=system" -w secret
At this point, the LDAP server configuration is complete.
JDK Import Certificate #
Since the LDAP server uses a self signed certificate, you need to import it into the keystore of JRE before accessing the client.
Note: During the import process, you need to enter the key of the certificate: secret.
keytool -import -alias localhost -keystore $JAVA_HOME/jre/lib/security/cacerts -file /Users/${yourname}/apacheds/localhost.cer
Proxy-LDAP Test #
a. server.yaml
authority:
users:
- user: root@%
- user: admin
- user: sharding
authenticators:
auth_ldap:
type: LDAP
props:
ldap_server_url: ldap://localhost:10389
ldap_dn_template: uid={0},ou=system
defaultAuthenticator: auth_ldap
b. Start Proxy.
c. Start Wireshark and start capturing packets on port 10389.
d. MySQL client login test.
Note that the parameter –enable-cleartext-plugin is specified.
# Since there is only one admin user in the LDAP server, use admin to log in.
# If you try another user, the result is login failure.
mysql -h 127.0.0.1 -P 3307 -A -u admin -p --enable-cleartext-plugin
Login succeeded after entering the password secret:
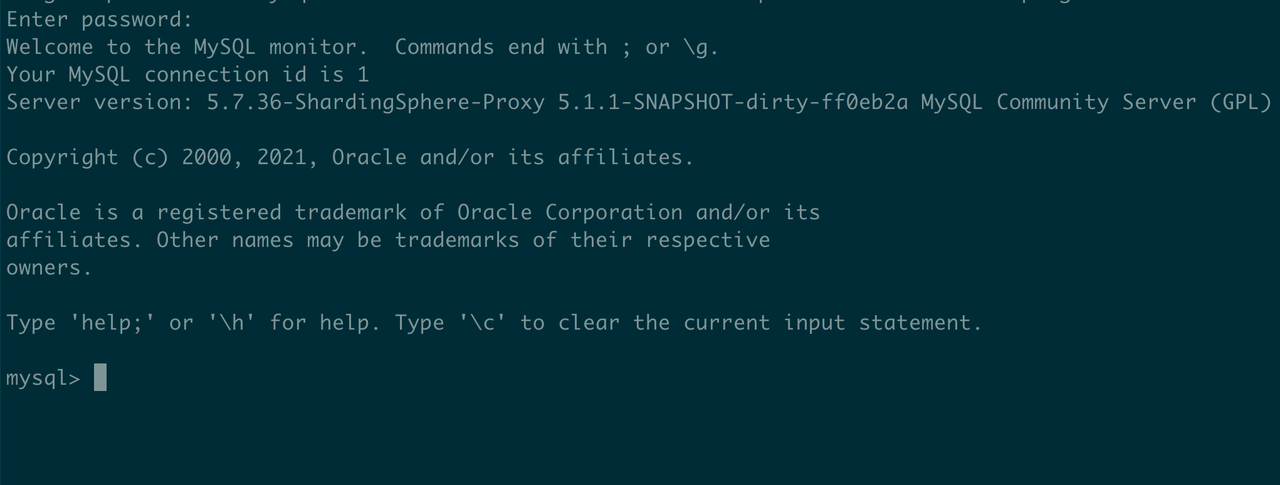
e. View packet capture data.
From the captured TCP packet, we can easily find a message containing user DN and password:
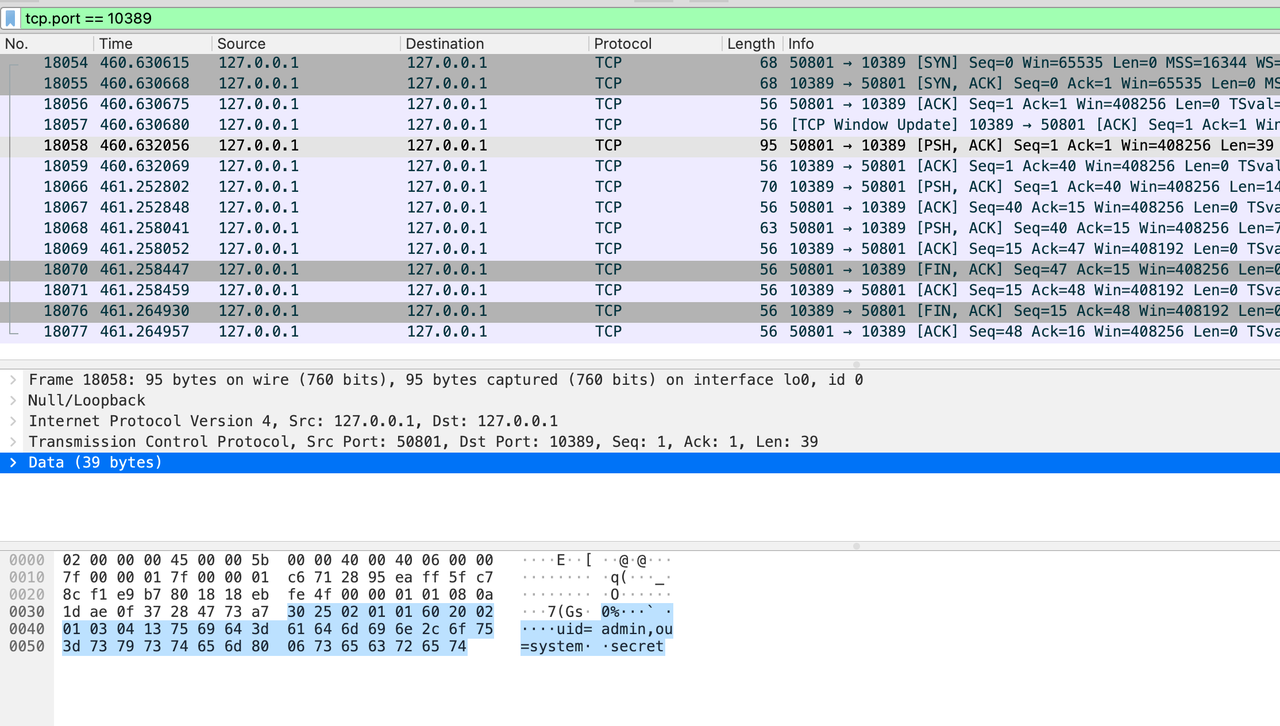
f. Summary
From server.yaml configuration, we can see that under the premise of existing LDAP server, using LDAP for login authentication is not complicated, and only simple configuration is required.
On the other hand, because LDAP protocol is unencrypted, there is a risk of password disclosure when using LDAP authentication in public networks.
Proxy-LDAPS Test #
a. server.yaml
The only difference from the LDAP case is that the URL of the LDAP server is changed.
authority:
users:
- user: root@%
- user: admin
- user: sharding
authenticators:
auth_ldap:
type: LDAP
props:
ldap_server_url: ldaps://localhost:10636
ldap_dn_template: uid={0},ou=system
defaultAuthenticator: auth_ldap
b. Start Proxy .
c. Start Wireshark and start capturing packets on port 10636.
d. MySQL client login test.
Note: need to specify the parameter –enable-cleartext-plugin.
# Since there is only one admin user in the LDAP server, use admin to log in.
# If you try another user, the result is login failure.
mysql -h 127.0.0.1 -P 3307 -A -u admin -p --enable-cleartext-plugin
Login succeeded after entering the password secret:
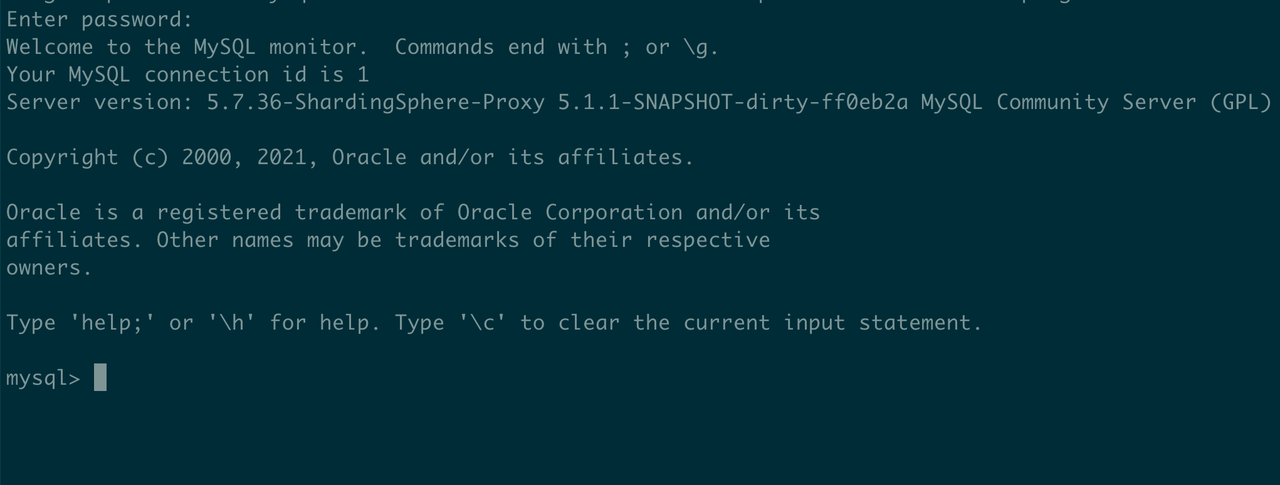
e. View packet capture data.
It can be seen from the data packet that TLS communication has been established between proxy and LDAP server, and the content of communication cannot be obtained through packet capturing:

f. Summary
SSL/TLS encryption can effectively protect user login information. The SphereEx-DBPlusEngine is very friendly to LDAPS. You can switch from LDAP to LDAPS by importing certificates and replacing URLs.